VMI Report: 48% of Organizations Face BYOD Data Breaches

Key Findings from the annual Virtual Mobile Infrastructure (VMI) Report: Trends in Secure Mobile Access & BYOD
The numbers are staggering, and they should concern every security and compliance leader in information technology: approximately 48% of organizations have suffered data breaches linked to unsecured or unmanaged personal devices in the past year. As the bring-your-own-device (BYOD) market explodes from US $129.2 billion in 2024 to a projected US $331.6 billion by 2030, the attack surface isn't just growing—it's becoming exponentially more dangerous. This growth mirrors the expansion of the virtual mobile infrastructure market, which is evolving to address these mounting security concerns.
The Growing Threat That Won't Go Away
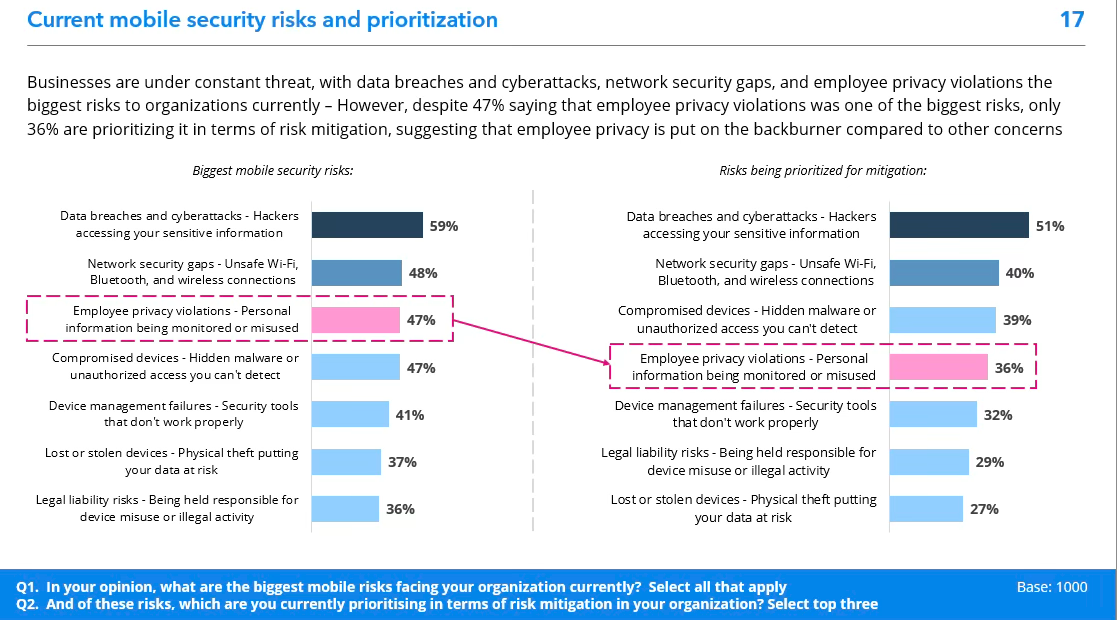
Organizations across every industry vertical face a complex mobile threat landscape characterized by escalating risks. According to the annual VMI Report, 59% of surveyed organizations cite data breaches and cyberattacks as their top concerns, with 48% pointing to network security gaps and 47% worried about compromised devices. Yet many organizations continue to rely on the same outdated Mobile Device Management (MDM) and enterprise mobility management solutions that were designed for a different era, a different threat landscape, and a fundamentally different way of working.
These legacy tools attempt to secure corporate data by imposing controls on personal devices—whether through configuring mobile client settings, managing profiles, or restricting mobile apps—but they're creating security gaps through their fragmented approach. The result? Nearly half of all organizations are experiencing exactly what these tools were supposed to prevent: data breaches stemming from mobile access across mobile networks.
The cost extends far beyond the immediate data loss. Such as:
- Compliance violations that trigger regulatory fines.
- Reputation damage that erodes customer trust.
- Operational disruption that hampers productivity for every software engineer and end user.
- And perhaps most critically, the false sense of security that prevents organizations from recognizing they have a problem until it's too late.
The Productivity Price of Security
To understand the true state of mobile security, Hypori commissioned independent research conducted by Sapio Research. The resulting annual VMI Report, based on a survey of 1,000 security, risk, mobility, and BYOD decision-makers in organizations with more than 1,000 employees globally, reveals a critical blind spot: 69% of organizations report that their current mobile security controls have negatively impacted end-user productivity or satisfaction, with 24% stating the impact on user experience has been severe.
In North America specifically, 72% report that mobile security controls negatively impact user productivity—whether through restrictive kiosk mode implementations, cumbersome web clip deployments, or complicated administration settings. This isn't a minor inconvenience—it's a systemic issue undermining the very tools meant to protect organizations.
Yet despite widespread recognition that privacy violations are among the most significant risks—with 47% citing employee privacy violations as one of their top concerns—only 36% are actively prioritizing privacy violations in their mitigation strategies. This gap between recognition and action creates organizational blind spots that leave companies vulnerable while simultaneously eroding employee trust.
Rethinking the Equation
The reality is stark: you cannot secure what you cannot control, and you cannot control devices you don't own. This fundamental truth is driving a shift in how forward-thinking organizations approach mobile security.
The reality is stark: you cannot secure what you cannot control, and you cannot control devices you don't own. This fundamental truth is driving a shift in how forward-thinking organizations approach mobile security in the era of remote work.
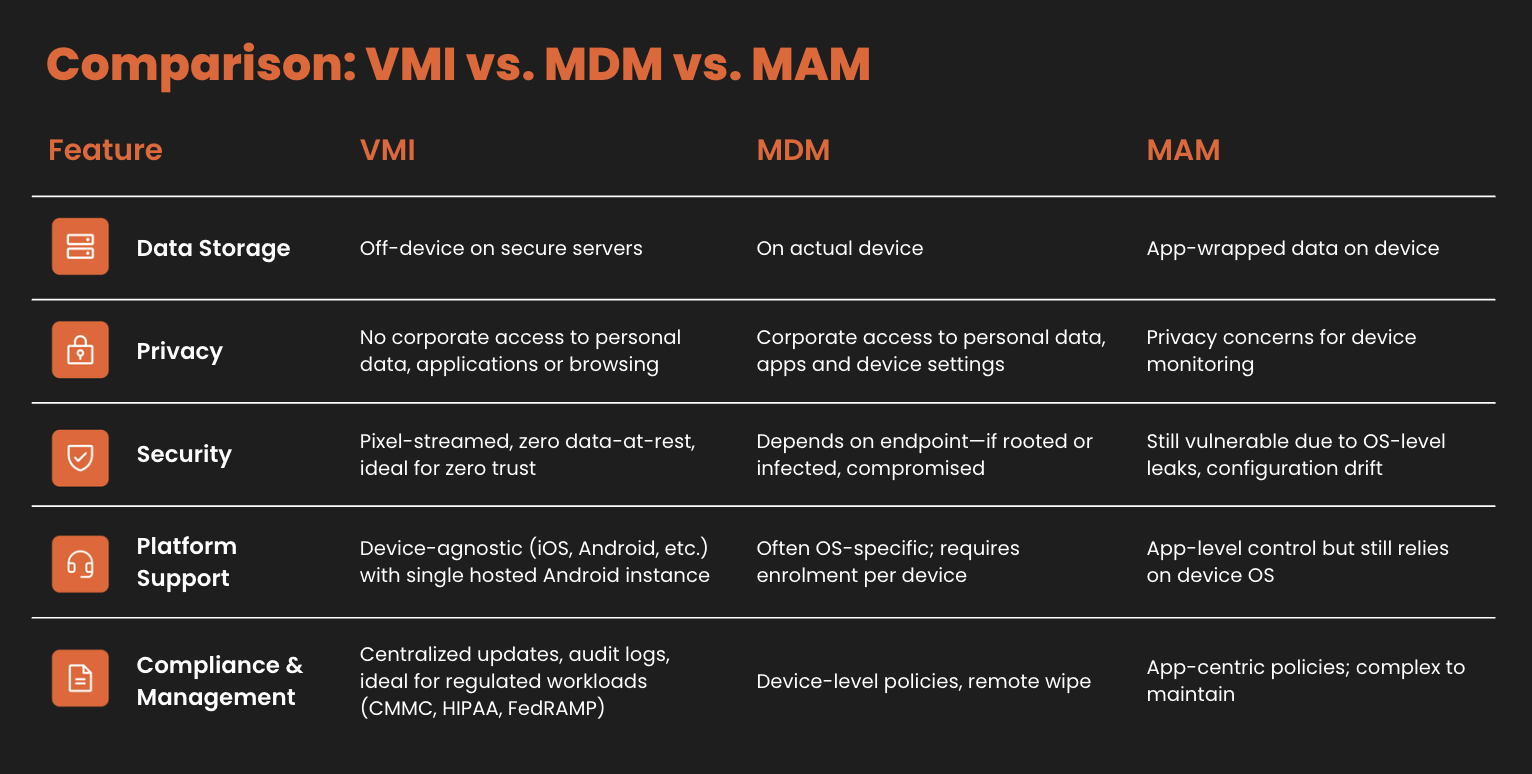
A VMI platform offers a different path—one that removes the device from the risk equation entirely. Instead of trying to manage and secure thousands of personal devices with varying security postures, VMI delivers secure, seamless access to enterprise apps and mobile applications from any device, anywhere, while keeping all sensitive data within a controlled cloud infrastructure. Unlike traditional virtual desktop infrastructure or desktop virtualization approaches, VMI is purpose-built for mobile-first environments.
The approach aligns naturally with zero trust principles. In North America, where regulatory scrutiny around data privacy and compliance is accelerating the move toward zero trust architectures, the alignment is particularly strong: 90% of North American respondents believe VMI aligns with zero trust principles. Rather than trusting the device (which is inherently risky in a BYOD environment), VMI shifts trust to the infrastructure—where data never resides on the endpoint, never travels unencrypted across any mobile virtual network operator, and remains under enterprise control at all times. Each user workspace remains completely isolated and secure.
Despite North America leading in mobile security maturity—with 49% of organizations considering their security posture "very mature," the highest of any region—the reality is that even these mature organizations face the same fundamental challenge: traditional MDM/MAM solutions are no longer fit for purpose.
For organizations grappling with the reality that traditional MDM/MAM solutions are no longer fit for purpose, VMI represents more than an alternative—it's a fundamental rethinking of mobile security architecture. One that addresses the actual threat landscape rather than the one that existed a decade ago. In fact, 57% of North American respondents expect VMI to have the greatest impact on secure mobility in the next three years—the highest percentage globally, signaling where the industry is headed.
The Time to Act Is Now
With mobile devices serving as the primary work interface for an increasingly distributed workforce, the stakes have never been higher. The 52% year-over-year increase in mobile attacks isn't slowing down. And as the BYOD market continues its explosive growth, the problem will only intensify.
The organizations that recognize this reality—and act on it—will be the ones that thrive. Those that continue with legacy approaches will likely become statistics in next year's report.
Download the full report.
Recent articles
%20(28).png)
The Future of Secure Mobility: Why VMI is the New Standard for BYOD
Secure the data, not the device. Hypori VMI isolates the workspace to leave zero data on the phone, ensuring Zero Trust security and user privacy.
%20(27).png)
The Secure Night Before Christmas: A Look Ahead at 2026 Cybersecurity Predictions
Hypori’s Chief Security Officer shares 2026 cybersecurity predictions: Why zero trust and intelligent data separation are replacing traditional device-centric security strategies.
%20(24).png)
Why CMMC Compliance Starts with Mobile CUI Security
In this special edition of the Stern Report, Laura Schwab, Director of PR and Channel Marketing at Hypori, sat down with CSO Matt Stern to discuss the challenges of modern enterprise mobility.
%20(16).png)
What Is Virtual Mobile Infrastructure (VMI)?
Discover how VMI keeps enterprise data off personal devices, enabling secure BYOD and zero-trust mobility for regulated industries.

BYOD & MDM vs. Virtual mobility
Discover the benefits, pitfalls, and costs of BYOD, MDM, and virtual mobility solutions. Learn how to choose the best mobile program for your organization based on insights from Gartner's latest report.


