What is Mobile Device Management (MDM)?

Mobile Device Management (MDM) was largely considered the only option for organizations looking to roll out bring-your-own-device (BYOD) or mobility programs to their employees. In theory, MDM solutions promise the perfect balance of security and flexibility.
But here's what many IT leaders have discovered: that balance is increasingly difficult to maintain. IT and security team wants one thing. Your employees want another mainly in the form of more personal privacy. Not to mention you have to take into consideration costs and scalability.
At Hypori, we've pioneered an entirely different approach to the BYOD security challenge. After working with organizations with the strictest security requirements, we've developed a solution that satisfies both security teams and end users.
By the end of this article, you'll understand why leading organizations are moving beyond traditional MDM. We also discuss the benefits of embracing virtual BYOD solutions for better security.
What is MDM and Why Does It Exist?
MDM emerged from the need for organizations to secure sensitive data on employee’s mobile devices as well as a way to control and monitor their usage. As companies expanded, enterprise mobility management became a key component of their security infrastructure.
Traditional MDM platforms provide IT administrators with tools to:
- Enforce security policies across employee devices
- Configure device settings and restrictions remotely
- Deploy and manage corporate applications
- Track device location and usage
- Wipe corporate data when necessary
If employees want to access company resources on their phones, the company should have some control over those devices to protect sensitive information.
This became particularly important as smartphones evolved from simple communication tools to powerful computing devices. They now have the ability to store and process enormous amounts of corporate data.
How MDM Software Works Across Mobile Devices
In a typical MDM solution, companies require employees to "enroll" their devices by installing a management profile. This profile gives the MDM platform special privileges to control various aspects of the device.
Once enrolled, the MDM server can push configuration profiles to devices. It defines everything from password requirements to which apps can be installed. IT administrators gain visibility into device status, compliance, and potential device usage patterns.
The MDM agent running on the device creates a communication channel back to the corporate MDM server. This then allows ongoing monitoring and management. When employees leave the organization or devices are lost, IT can remotely wipe corporate data. In some cases, it can even wipe the entire device.
The Benefits of Implementing an MDM Solution
Traditional MDM does offer meaningful benefits to organizations:
- Reduced Security Risk: By enforcing encryption, strong passwords, and other security policies, MDM helps prevent data breaches through lost or stolen devices.
- Easier Compliance: For regulated industries, MDM provides mechanisms to demonstrate control over company data to meet requirements like HIPAA, or CMMC.
- Remote Control: When issues arise, IT can troubleshoot, update, or even wipe devices without having physical access to them.
- Inventory Management: Organizations gain visibility into what devices are accessing corporate resources and their security status. This makes asset management significantly more efficient.
These benefits have made MDM a standard component of enterprise mobility strategies for large fleets of corporate-owned devices. But what about employee-owned devices?
BYOD and Mobile Device Management
BYOD programs emerged as employees increasingly preferred using their own smartphones and tablets for work. The potential benefits of using familiar devices include cost savings, employee satisfaction, and productivity gains.
However, BYOD created an immediate tension with traditional MDM approaches. The question became:
How much control should an organization have over an employee's personal property?
Consider what a standard MDM deployment on a personal device typically means:
- Corporate IT can see what apps you've installed or what websites you’ve visited
- They can enforce restrictions that affect your personal use
- They might have the ability to track your location
- They can potentially wipe your entire device, including personal photos and data
This level of intrusion has led to significant employee resistance. Many workers simply refuse to enroll their personal devices in MDM programs. This creates shadow IT problems where sensitive data flows through unmanaged channels.
Organizations have tried to find a middle ground through Mobile Application Management (MAM) or "containerization." Here, the systems attempts to separate work and personal data. However, these compromises often create clunky user experiences while still requiring significant device access.
The Hidden Challenges and Limitations of Traditional MDM
Beyond the obvious privacy concerns, traditional MDM suffers from several critical limitations. Unfortunately, many organizations only discover these after implementation:
- Employee Resistance and Workarounds: When MDM policies are too restrictive, employees find creative ways to bypass them. This often creates worse security problems than having no MDM at all.
- Management Complexity: Maintaining an MDM system across different operating systems, versions, and device types becomes increasingly complex and resource-intensive.
- Limited Control: Despite their invasiveness, MDM tools often can't prevent determined users from extracting corporate data through screenshots, personal email, or other channels.
- Legal and Liability Issues: Monitoring personal devices creates potential legal exposure, particularly across different jurisdictions with varying privacy laws.
- Productivity Impacts: Overly restrictive MDM policies can hamper legitimate work activities and frustrate employees.
Perhaps most critically, the fundamental model of MDM creates an inherent vulnerability. If a device is jailbroken, infected with malware, or physically compromised, MDM protections can be bypassed.
A Better Approach: Virtual Mobile Access vs. Traditional MDM
What if there was a way to give employees secure access to corporate resources without requiring any control over their physical devices?
This is where virtual mobility technology enters the picture.
Rather than attempting to secure data on the physical device, virtual mobility platforms create a completely separate, virtual smartphone that runs in a secure cloud environment. Employees access this virtual workspace through their physical device, but no corporate data ever touches the employee's actual phone.
The physical device simply displays an encrypted pixel stream from the virtual device. All processing, data storage, and security controls happen in the cloud environment, not on the employee's phone.
This approach delivers several critical advantages:
- Complete Separation: Corporate data never touches the employee's physical device, eliminating the risk of data leakage through a compromised phone.
- No Privacy Concerns: Since the organization has no access to or control over the personal device, employee privacy is preserved.
- Consistent Experience: The virtual workspace can provide a consistent experience across any device type, simplifying support and training.
- Enhanced Security: Even if the physical device is compromised, lost, or stolen, corporate data remains protected in the cloud environment.
Mobile Device Management Best Practices
Whether you're using traditional MDM or exploring virtual alternatives, certain best practices should guide your approach to mobile management:
- Establish Clear Policies: Define precisely what data can be accessed on mobile devices and under what conditions.
- Balance Security and Usability: The most secure system is worthless if employees won't use it. Find the right balance that protects critical assets without creating unnecessary friction.
- Employ Multi-Factor Authentication: Regardless of your approach, MFA provides an essential additional security layer for mobile access.
- Adopt Zero Trust Principles: Assume devices could be compromised and design access controls accordingly.
- Educate Users: Help employees understand the security risks and their role in protecting company data.
- Consider Device Context: Adapt security requirements based on device type, ownership, and usage context.
- Plan for Incidents: Develop clear procedures for handling lost devices, employee departures, and potential breaches.
For organizations struggling with traditional MDM challenges, the most important best practice may be: consider whether there's a better approach altogether.
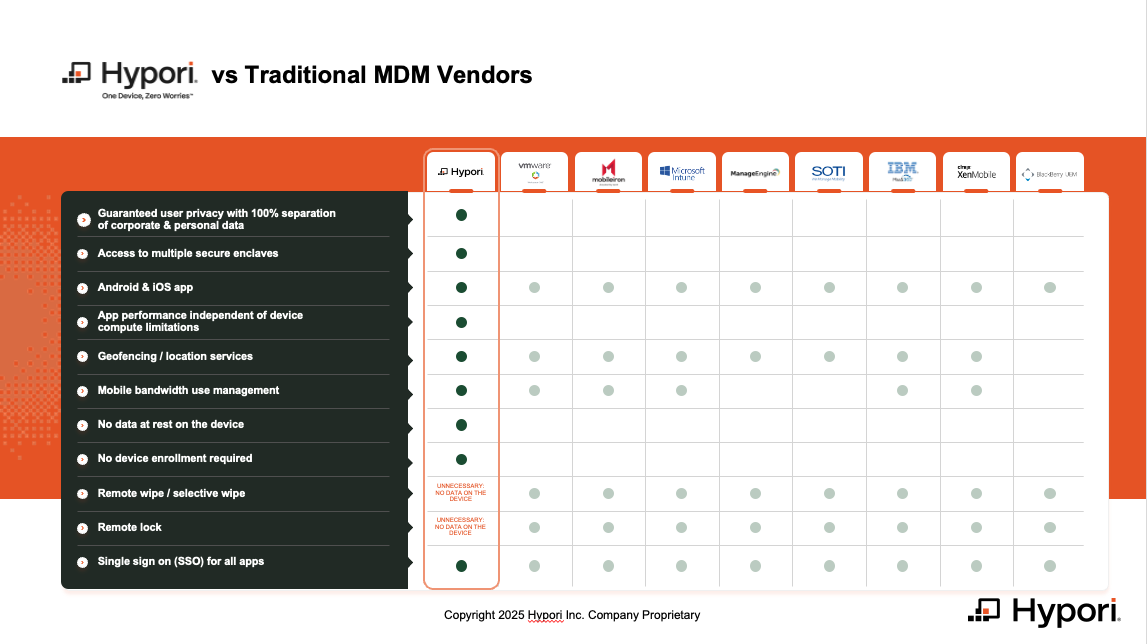
Hypori: A Zero Trust Virtual BYOD That Employees Actually Like
Hypori has reimagined mobile security from the ground up by asking a simple question:
What if we could give employees the access they need without requiring any control over their personal devices?
Our mobile access / BYOD platform creates a completely separate, cloud-hosted virtual device that employees access through a simple app on their phone or tablet. All corporate data, applications, and processing happen in the virtual environment. This means it never touches the employee's physical device.
This approach delivers powerful benefits:
- Zero Data at Rest: Since no corporate data is stored on the physical device, lost or stolen phones present no risk of data breach.
- Complete Privacy: The Hypori app has no special permissions on the employee's device and can't access personal data, photos, or communications.
- Simple Deployment: No complex MDM profiles or device enrollment - just a simple app download.
- Consistent Experience: The same secure virtual environment works across iOS, Android, and Windows devices.
- Enhanced Security: Hypori's virtual devices run in zero-trust cloud environments, leveraging enterprise-grade security controls far beyond what's possible on consumer devices.
The result? Security teams get better protection than traditional MDM could ever provide, while employees maintain complete privacy and control over their personal devices.
The Future of Mobile Security is Virtual
As mobile threats continue to evolve and privacy concerns intensify, the limitations of traditional MDM become increasingly apparent. Trying to secure data on devices you don't fully control is fundamentally problematic.
Virtual mobile access technology represents the next evolution in mobile security - addressing the core challenges of BYOD by completely separating corporate and personal environments.
For organizations struggling with MDM resistance, security gaps, or management complexity, solutions like Hypori offer a compelling alternative that satisfies both security and usability requirements.
Take the Next Step Toward Better Mobile Security
If your organization is facing MDM challenges or looking to modernize your approach to mobile security, it's time to explore how virtual mobilization can transform your mobile strategy.
Ready to see how virtual BYOD can solve your mobile security challenges? Request a demo with Hypori for a personalized demonstration of our zero trust virtual access platform.
Don't compromise on security or employee experience - with the right approach, you can have both.
Recent articles
%20(30)%20(1).png)
Secure Messaging for Enterprise: Hypori vs Signal vs WhatsApp
Secure messaging apps compared: Hypori, Signal, and WhatsApp. The real security gap isn't encryption, it's data exposure on personal devices.
%20(31).png)
The BYOD Identity Crisis
BYOD security risks go beyond data breaches. The real threat is the privacy-versus-control conflict eroding trust and creating legal exposure for organizations.
%20(30).png)
Zero Trust Mobile Authentication: How It Works and Why It Matters
Zero trust mobile authentication continuously verifies every access request—no device is trusted by default. See how it works and why enterprises need it.

BYOD & MDM vs. Virtual mobility
Discover the benefits, pitfalls, and costs of BYOD, MDM, and virtual mobility solutions. Learn how to choose the best mobile program for your organization based on insights from Gartner's latest report.

8 Most Common Remote Access Vulnerabilities
Discover the top 8 remote access vulnerabilities putting your organization at risk and learn practical solutions to protect sensitive data and secure your workforce.

The Future of Secure Mobility: Zero Trust for CUI Protection
Hypori attended CyberScoop's Zero Trust Summit and shares how Hypori’s zero trust approach protects CUI and FCI on mobile devices—without MDM.


