How it works
Only encrypted pixels are transmitted to and from the physical device.
User’s physical device is a “window” to their virtualized smartphone residing in the cloud or on-prem.
Hypori Halo app captures touch and sensor data from any iOS, Android, or Windows 10 device.
Zero-trust architecture protects data and user privacy.
Hypori’s Defense Isolates to Protect
The Hypori Halo secure virtual device provides an unparalleled defense in depth to isolate and protect privacy, personal data, and organizational data; eliminate data at rest requirements from the physical device; minimize the risk of data loss; and essentially eliminate the risk of introduction of malware into an enterprise from an end user device.
End users install the Hypori Halo App on their existing Android, iOS, or Windows 10 device, providing a secure and convenient method for accessing their Hypori Halo virtual device. The Hypori Halo App uses FIPS 140-2 validated components for key protection and TLS 1.2 encryption, supports PKI credential-based multi-factor authentication, and is NIAP Common Criteria certified.
Enables enterprise identity and access management via AD & LDAP integration.
Provides superior multimedia experience with performance-optimized voice, video, and data.
Supports PKI credential-based multi-factor authentication.
Supports enterprise-class storage integrations, including NAS and SAN storage.
see Hypori Halo in action
In this 80-second video, see how fast and easy it is to access your secure virtual Android device from this Apple smartphone.
Easy to Deploy. Easy to Manage. Your IT team will thank you.
Download the Hypori Halo app from the Google Play store or Apple store, provision based on user profile, manage every device from a single pane of glass Administrative Portal.
Centralized Hub for Simple Administration
SaaS delivery from the cloud allows system administrators to easily manage authentication, provisioning, virtual workspace hosting, and APIs.
One screen to manage it all. Out-of-the-box integrations with monitoring, reporting, and MAM systems are also available.
Isolation means more than just security & Privacy
Hypori Halo’s unique separation of secure environments means:
Zero-trust access to multiple virtual workspaces from a single device
Quick user adoption for BYOD at scale
White House OMB M-23-13 Compliant
Total separation between personal and corporate workspace data
100% user privacy
Zero risk of data leakage
No threat of malware entering the corporate workspace
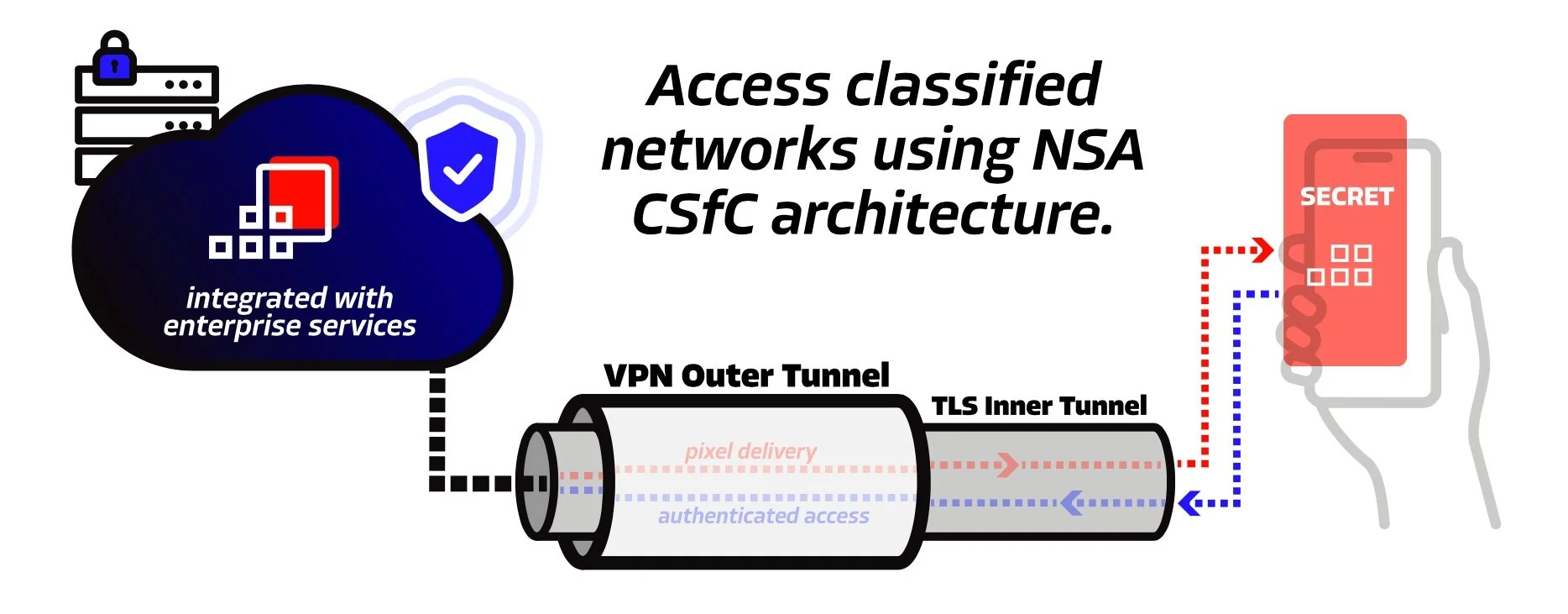
Securing Our Nation's Most Sensitive Data
Originally developed to enable secure access to classified networks using managed government-furnished equipment (GFE), Hypori is an authorized NSA Commercial Solution for Classified (CSfC) programs vendor* solving the “no data in transit” and “no data at rest” problem for our most sensitive customers.
*Hypori is currently under contract with Leidos, Inc. Common Criteria Testing Lap to meet renewal evaluation CSfC TLS.hypori HALO for Defense and regulated industries
Hypori Halo addresses the complex challenges of data security on personal devices across industries.